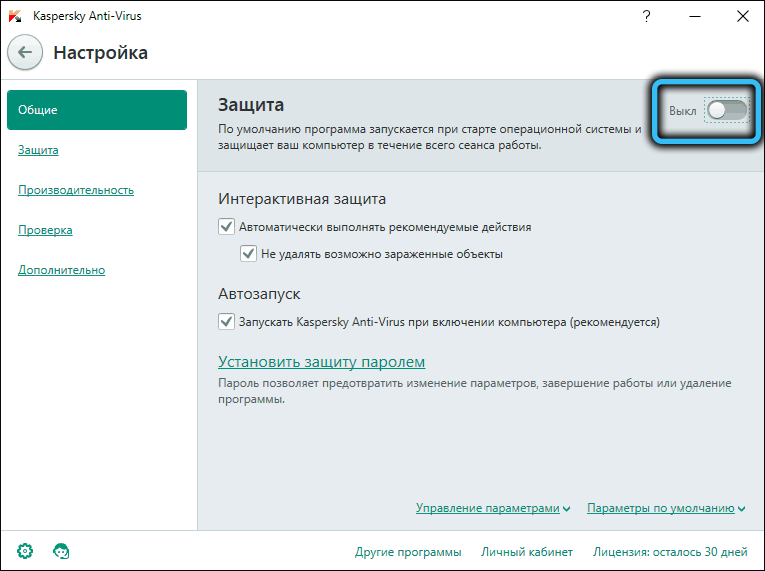
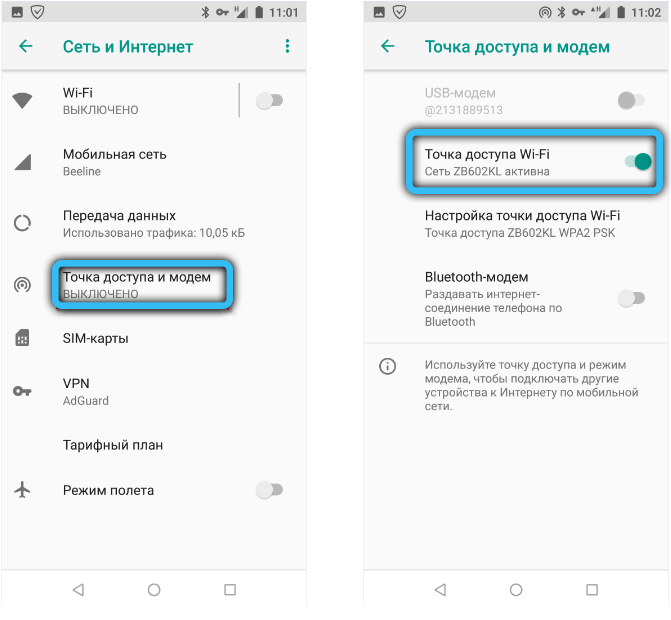
The number of threats in the modern digital world is constantly growing in parallel with the improvement of means of protection against them. The emergence of two- and even three-factor authentication systems, of course, significantly reduces the likelihood of losing…
Category: Programs
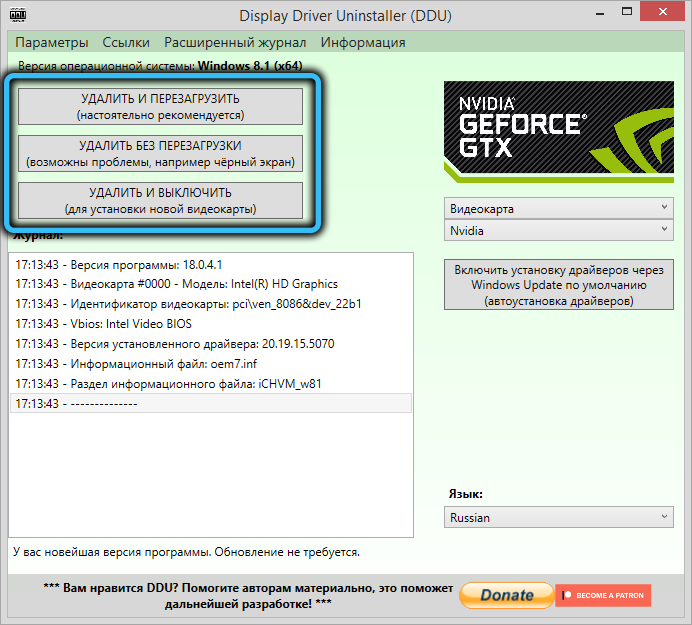
Using the Display Driver Uninstaller (DDU)
Video card drivers are usually updated more often than others. At least, if the computer user has not refused updates. Often, after the next update, you may notice that the video card began to work with oddities. What do they…
Cloning disks with Macrium Reflect
Sooner or later, any PC user is faced with the need to reinstall the operating system. And regardless of where Windows will be installed, on a new or old disk, HDD or SSD, in many cases it is advisable to…
Clone Windows with Samsung Data Migration
Upgrading a computer is not such a rare procedure, given that the amount of stored data is constantly growing, and the capacity of the existing drive becomes insufficient over time. But replacing a disk, especially an SSD drive, is a…
Nahimic program: purpose, use, removal
The improvement of computers takes place in different directions. While Intel and AMD vie with each other to miniaturize the die-making process, there are advances in audio processing. And here the efforts of the developers are also divided: some specialists…
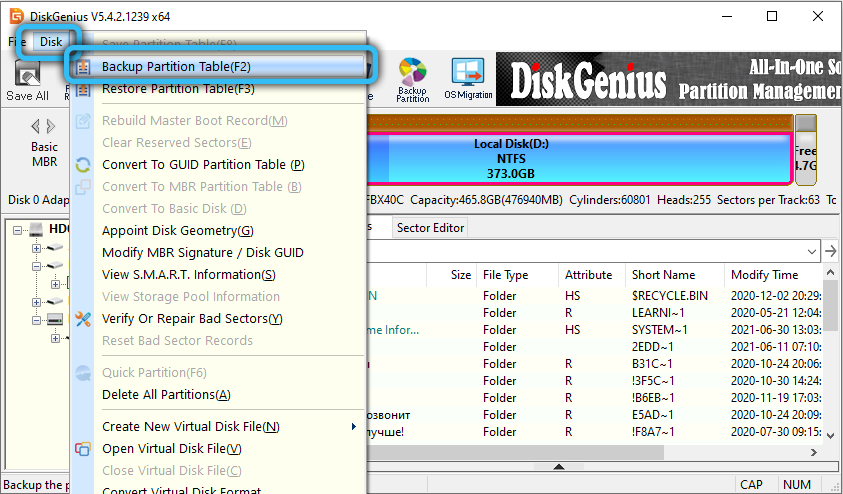
Disk Utility DiskGenius Features
The basic capabilities of the built-in Windows disk tools are sufficient for many tasks, but many advanced users, not to mention system administrators, prefer to use third-party utilities that have much more power. One of them is the DiskGenius program,…
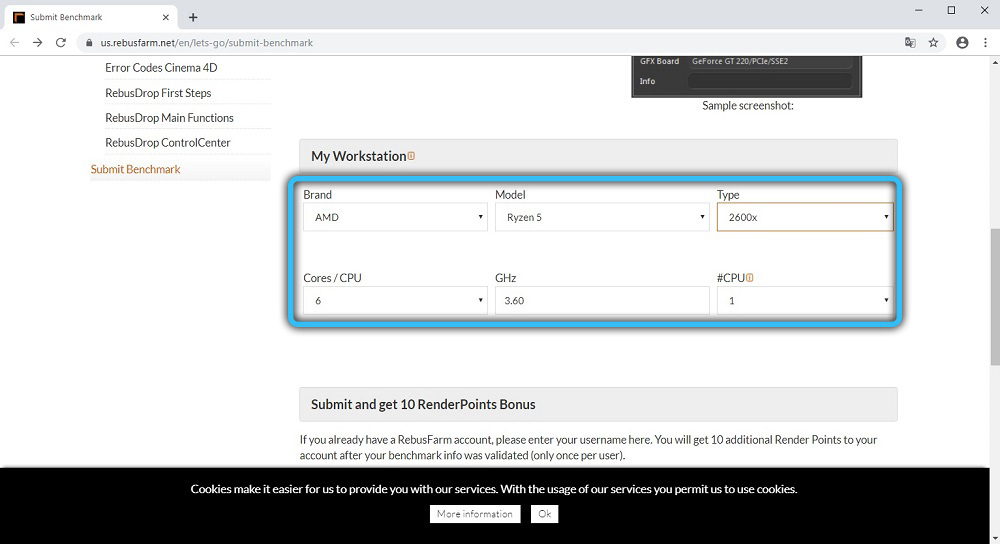
Features of CPU performance testing using Cinebench
Comparative testing is a generally accepted way to find out which manufacturer’s product is better. When it comes to computers, here such testing is designated by a special term – benchmark. Initially, it was understood as testing the performance and…
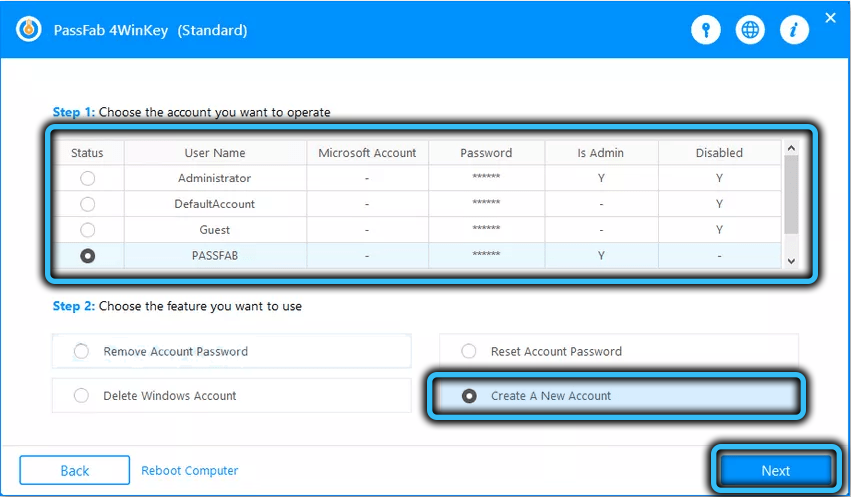
Using PassFab 4WinKey to Remove or Reset Windows Passwords and Accounts
Everyone is concerned about the problem of cybersecurity today – from software manufacturers to manufacturers of wearable gadgets – it is no coincidence that new authentication means are being introduced into everyday life – by fingerprint, face control, graphic password.…
How to download a file that is blocked by Google Chrome
The unprecedented security measures introduced in Windows 10 are not always sufficient. Moreover, even antivirus software is not always able to protect your computer from external threats. It is no coincidence that even common browsers have functionality that makes surfing…
What to do if the site is marked as “Not secure” in the browser
The problem of network security is becoming more and more urgent, so the de facto modern standard for sites is to use the secure https protocol. Unfortunately, the professionalism of the developers in this regard is still lame, so in…