The Wikileaks website calls this the largest information leak in the history of the United States Central Intelligence Agency (CIA). Dubbed Vault 7 , this Wikileaks post includes information on how the CIA can hack, intercept, and take control of devices and equipment around the world .
The CIA has a worldwide hacking program , with thousands of people working to develop programs that can infiltrate millions of mobile devices or systems, whether online or offline . Even invade web servers and internet infrastructure .

Through viruses and other malicious software , it could automatically infect and gain control of cell phones, computers, TVs, routers, and even modern automobiles (in the latter case, for murderous purposes, according to Wikileaks). Through other tools the software can intervene on CDs and DVDs . The agency is also able to extract information from isolated internet systems , such as a police database, using a simple USB memory stick and the physical intervention of a person.
Contents
CIA intercepts WhatsApp before data is encrypted
You can covertly activate the microphone and camera of smartphones or webcams . You can also get the location, intercept calls and messages from these devices. Applications like WhatsApp, Telegram or Signal certainly ensure communication between both ends, but the CIA is capable of intercepting these communications, before those applications can protect the transmitted information .
The problem is in the operating systems
It is not a problem of the applications themselves, but of the operating systems on smartphones, such as Android and iOS . The CIA has teams of people specialized in finding security holes in these platforms. They are vulnerabilities that neither Google nor Apple themselves manage to detect to be corrected. That is, the solution is not to improve the applications, but rather that the manufacturers patch the weaknesses in the software of their equipment.
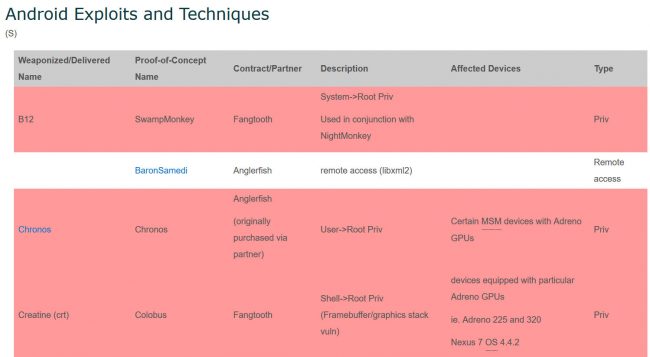

Exploits and techniques used by the CIA to exploit vulnerabilities in the Android system
Fake shutdown on Samsung Smart TVs
The CIA intervenes Samsung smart TVs in a particular way. They implement a false shutdown mode . The computer appears off to the user, but is actually on, recording a potential conversation in the environment and sending the information to the CIA computers.
CIA malware is not detected by antivirus
Those malicious programs can collect all the information that a person enters by keyboard on their device. They can also collect all user passwords , capture via webcam , destroy data, etc. Unfortunately, they are also capable of evading the detection of reputable antivirus . Through various maneuvers, they are programmed to stay days or even years on the target device . Their code and form of communication are designed to prevent them from eventually becoming involved with the CIA or the United States government.
Hacking tools held by other entities
The vulnerabilities exploited by these CIA weapons are unknown to equipment manufacturers. Although the CIA could, and indeed should, report them to companies, it does not do so because it ensures that it can continue to hack any device . The most serious problem is that the CIA has previously lost control of many of these malicious hacking tools , through former employees. Now they can be found in the hands of other hackers , companies , organizations or even governments that will also have the power to hack the entire world . This is exactly how this information has reached the Wikileaks website.
Update March 9, 2017 : Google has reported that it has already fixed “many” of the vulnerabilities mentioned by the CIA, in Chrome and Android. He says they have a scan in progress and will implement any other necessary protection.
References : Wikileaks
Police can now legally spy on people’s WhatsApp in Germany
How to know if your WhatsApp is spied, cloned, hacked or intervened
How to PROTECT my cell phone from viruses, spies, interventions, etc.
Receive updates: SUBSCRIBE by email and join 10,000+ readers. Follow this blog on Facebook and Twitter.