Contents
Researchers found a database, the content of which allowed conclusions to be drawn about the identity of millions of Whisper users. Bizarre data evaluations included.Reading time:2 min.Save in pocketRead outPrintviewRead comments6posts
The mobile app Whisper for Android and iOS has been around since 2012. It serves users as a kind of anonymous social media channel, through which they give so-called “Whispers” – more or less piquant “confessions” – without specifying real names or addresses. can publish. Anonymous discussions, individual chats and the uploading of videos are also possible.
The founder of the company behind Whisper described the app in 2014 as the “safest place on the Internet”. It was already known at the time that the app was busy collecting data about its users, which, especially in combination with “Whispers” and other data, can provide information about their identity.
Among other things, each user is localized – based on their GPS coordinates or based on their IP address. Deleted Whisper messages also remain on the company’s servers. Whisper also makes no secret of data collection, evaluation and disclosure, including to third parties, in its privacy policy .
900 million records leaked with plenty of metadata
Security researchers have now reported to the Washington Post about an ElasticSearch-based Whisper database that was freely accessible online without password protection. How long the total access was possible and whether it actually took place is unknown. As of Monday, it is said to have been blocked by WhisperText LLC after the company was informed of the leak by researchers and journalists.
The Washington Post article speaks of 900 million records of user information collected from 2012 to the present. Little is known about the absolute number of users of the app, which was quite popular a few years ago: According to the app description on Google Play , more than 30 million people worldwide are still supposed to actively use it every month.
What is worrying is the large number of different metadata in the leak, which allow conclusions to be drawn about the originators of the “Whispers” and user videos (also available via the leak). In one article, The Register reports a total of 90 different metadata fields that were assigned to each user and only about five of which were intended to be displayed to other users in the context of the app. The data would have included age, gender, nickname, country, personal interests, IP addresses and time zones. But also more abstract information such as the number of published articles, nickname history or location information on the point in time of a certain article publication.
According to the Washington Post, there were also many minors among the users. For example, a search query for users who specified their age at the age of 15 would have returned around 1.3 million results.
“Sex Offender Probability” and Suicide Rates
Whisper’s App appears regularly on the Whisper App website, sometimes with a nickname and place of origin / country of origin. Whispers are shocking or otherwise entertaining. Many users, who in the context of the app also show a certain freedom of movement and carefree disclosure of intimate secrets, should be well aware of this marketing strategy of the app developers.
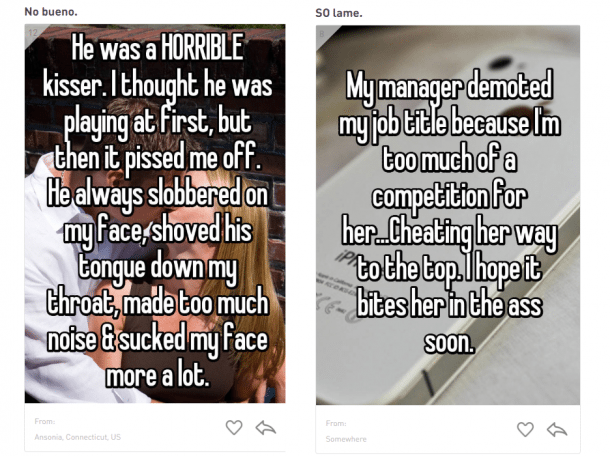
The problem with the data leak now is the possibility of linking these “secrets” to numerous potentially identifying metadata and possibly comparing them with other sensitive data after downloading the data. This type of access, which would not have been possible from the app, could have resulted in opportunities for extortion or attacks based on ethnicity or sexual orientation.
Or violence based on false accusations: According to the Washington Post, the leak also contains a metadata assignment with the title “predator_probability”. Apparently, the app developers had tried, based on unknown criteria, to predict whether a user should be banned from the community due to (virtual) sexual harassment of other users. An apparently hopeless endeavor that was ultimately discontinued: According to the Washington Post, 9,000 users had already achieved a score of 100 percent.
Take a close look at the installation
Another strange-looking attempt by the company to analyze the data was the attempt to search posts by people stationed in military bases (assigned by coordinates) for evidence of suicidal intentions. According to the Washington Post, a research project that the Whisper team wanted to offer to the US Department of Defense.
Ultimately, it is up to the app providers to protect the data collected from misuse. The current leak also reminds that users should read the respective terms and conditions before installing the app and also look closely at the rights they grant the app. In the case of Whisper, these rights include reading out contact data on the mobile device, accessing the exact location, camera, photos and other files, as well as information on incoming and made calls. Until the end of the long list is reached, enough time should elapse to rethink the installation.