With two-factor authentication, you can additionally secure your online accounts. Google is now going one step further and allows you to use the Android smartphone as a kind of hardware key.
If you are currently using two-factor authentication at Google, you will receive, for example, a web notification, email, phone call or SMS on your smartphone to confirm your identity when you log in or to refuse access. An alternative for more security is to buy a hardware key that uses Bluetooth, NFC or the USB port to verify yourself.
This is exactly what Google now offers and uses the Android smartphone as the hardware key. The company uses the FIDO2 standard for this . To be able to use the new process, your smartphone must have Android 7.0 or a newer Android version. Chrome OS, Mac OS or Windows 10 must be running on the PC you want to log in to, Bluetooth must be supported and a compatible browser must be available.
So you activate the new function
- Go to the Google security page
- Activates two-factor authentication here
- To do this, go to confirmation in two steps
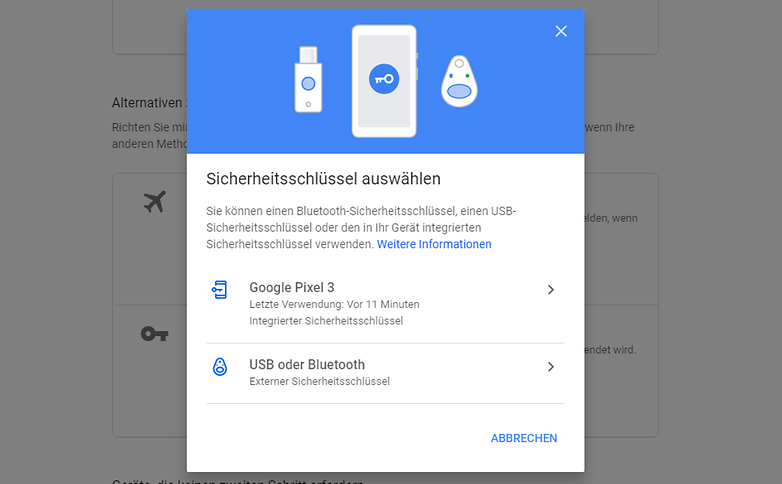
- Scrolls down to add security key
- Then you will see the list of devices that support the feature
- Select the appropriate device and tap Add
To be able to use the feature, you need to activate Bluetooth and location on the phone so that Google can establish the connection and check your proximity to the login location.
So you use the feature on your PC
- Activates Bluetooth on your PC (you do not have to actively connect to the phone)
- Logs into your Google account on the PC
- Checks the notification on your Android smartphone
- Confirms that you are trying to log in
- Follow the further prompt on the display
With the new method, your Google account and the data it contains is even a bit better protected. Google may extend the function and thus also secure the login to other websites.
