If your Internet is limited by a package of several gigabytes, then inevitably you have to monitor the volume of transmitted and received information – the so-called traffic. The Charles program helps with this: now we will figure out how to use it.
Contents
What is Charles
The program is designed for the Mozilla browser, so before installing Charles you need to download it. In principle, now the add-on is supported by both Google Chrome and Opera, but synchronization will require certain settings.
While you are surfing the Internet, the plugin collects information from servers and sorts them into folders with the names of the visited sites. You will see the amount of data going into and out of the network. The application does its job well enough to attract the attention of not only ordinary users, but also professionals.
Installing and configuring the program
You can download the distribution kit from the official website. There are two versions: free for a month and paid at a price of $ 50 per year. Don’t look for cracked variations of the plugin, as it will have to work with your data – in this case, you cannot rely on a product from an unknown source.
Installing Charles is easy – just follow the instructions that appear during the installation process. Unfortunately, the licensed version only offers English, but the button infographics are quite clear.
Also, for the Mozilla browser, download and install the latest Java version – this allows the program to work correctly. Sometimes the required file is put into a shared archive – click on it and run it. Please note that Java is not supported by Chromium-based browsers: Google Chrome, Yandex. Browser and others.
After installing the program, find the file with the .xpi extension in the installation package. Open Firefox and just drag and drop the item into the browser window.
Let’s go to the settings:
- If you have Firefox browser, then just open it, go to Tools – Charles tab and click Enable Charles. To check, open some site, and then Charles (the icon in the form of a jug, by default it is on the “Desktop”), and you will see a whole list of requests related to the opening of the resource.
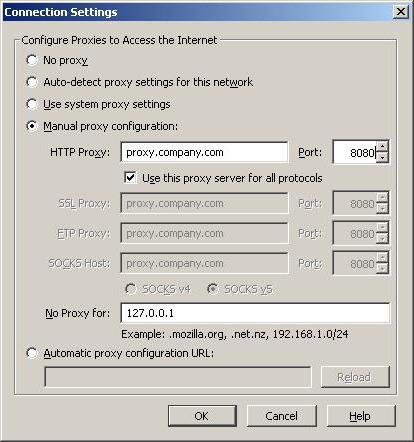
- In Chrome and Opera, you need to open “Settings” – “Proxy server”, check the HTTP item, specify IP: 127.0.0.1 and port: 8888.
How to use Charles: basic aspects
You have configured Charles, how to use it is immediately clear from the program menu:
- So that the data is not only tracked, but also recorded, click the Start / Stop Recording bar at the top – it is large, you will definitely not miss it. This is done in case there are any problems connecting to a specific site. Having a detailed report on the connection process, you can contact the system administrator, and he will quickly find the cause of the error.
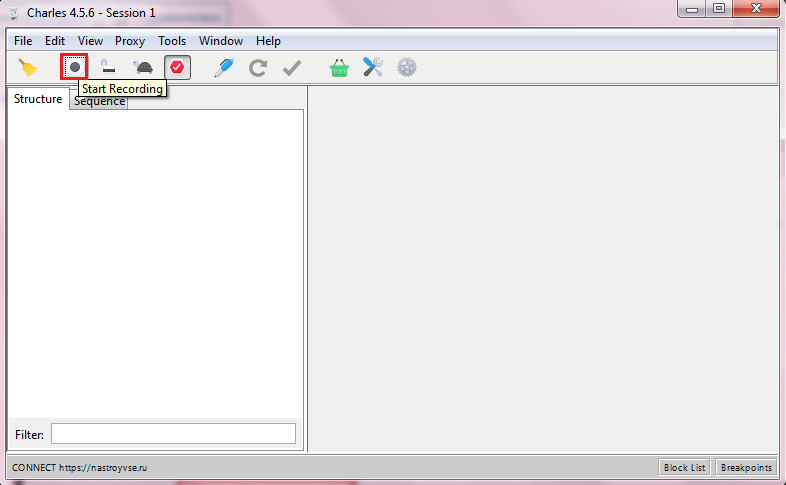
- If a site seems suspicious to you and you want to first understand what data it sends / receives, and then allow or prevent their movement, then you can make it so that, upon request in the browser, the information is transmitted directly to Charles. To do this, select the folder with its resource name, right-click on it and click Breakpoints – Enable / Disable Breakpoints.
- You can manage the contents of folders with information by clicking the additional button of the manipulator and the Edit command. After making adjustments to headers and other items, click Execute to submit the new contact form. You will receive responses to it from the server – you can view and save them for yourself. This is another plus in case of problems, encounters with fraudulent and phishing resources, etc.
Now you have figured out how to work with Charles. Even if you do not understand how to use the data, it is useful to store it in order to get help from the provider or system administrator in a timely manner.
Problems using Charles
Occasionally, when visiting some sites, information about them is not displayed in the Charles lists. Try the following:
- Open the Proxy / Recording Settings and Black List section.
- Remove the desired site from the latter, and its data will appear in the general list.
Also, a big problem with the program is that hackers use it. By skillfully manipulating the information received, they gain access to restricted content, for example, to closed objects in an online game. This is done by editing the information that came to Charles: first, the name and code of the available operation performed are recognized, and then the value is changed to a higher one. As a result, the player can “jump” several levels ahead and get premium resources. This poses a threat not only to developers of game entertainment, but also to rivals in the game, especially if competition is at the heart of it.
If you are tempted to do something like this, we strongly advise against doing this: as a rule, the developers follow the progress of the game, sooner or later they will discover your dishonesty, and you can lose your account along with all the achievements (and some people have been playing for years and have time make cash investments).