Stable operation of the Windows operating system is achieved through the functioning of many processes, some of which are simply hidden from the eyes of users. Such “secrecy” is characterized by the fact that the computer operator does not need to interfere with the work of these system processes, which explains the reluctance of users to pay attention to the activity indicators in the “Task Manager”. But this happens only for the time being, until the normal operation of Windows is disrupted, and then, in search of sources of excessive load, each user turns to the information in the “Task Manager” and sees that some processes have a special effect on the computer’s performance. And one of these “troublemakers” will be discussed in this article.
What is it
So, the process “Winlogon.exe” or “Windows Logon Application” is a system component that has an extensive set of functionalities for working with a user account. The structure of this component and all its powers have a rather complex structure, and it simply does not make sense to understand the wilds of it. To understand its importance, you can simplify the list of his to-do’s as much as possible and highlight the following points from them:
- Responsible for the safety of the desktop. Roughly speaking, every time a user sees a message about the need to enter a password to log into his account, this is just evidence of the success of “Winlogon”.
- Control over the integrity and safety of user data, “cooperating” with the “SAS” standard.
- Monitoring the activity of network connections.
- Confirmation of the legality of using the operating system version.
- Ensuring the proper functioning of screen servers (with active modes of operation).
Considering the importance of this functionality, it should be noted, and also taking into account that the executable file of the process in question is located in the system directory – C: Windows System32, its unauthorized deactivation can lead to short-term or long-term failures in the operating system. Therefore, if you have witnessed that in the “Task Manager” for “Winlogon.exe” or the “Windows Logon Program” (this may be its name), the indicators of the created load are highlighted in red, in no case should you complete it yourself work until the reasons for this situation are clarified.
Why is the load being created
The answer is simple. The work of “Winlogon” simply cannot create such a load that would directly affect the quality of the operating system. If there is such a load, then its culprit should be sought in a possible infection of the computer with virus software. It will not be a secret for anyone that various viruses are very fond of pretending to be system components, since “such a shell” creates a good guarantor of their inviolability. This statement is most directly related to the component considered in this article. Hiding a virus under the guise of “Winlogon” can be very appropriate and without careful study to reveal the “substitution” is extremely problematic. You should base your suspicions on the following points:
- During normal computer operation, there are no and cannot be two variations of Winlogon.exe in the Task Manager. If you see two representatives, then one of them is guaranteed to be a “spy”.
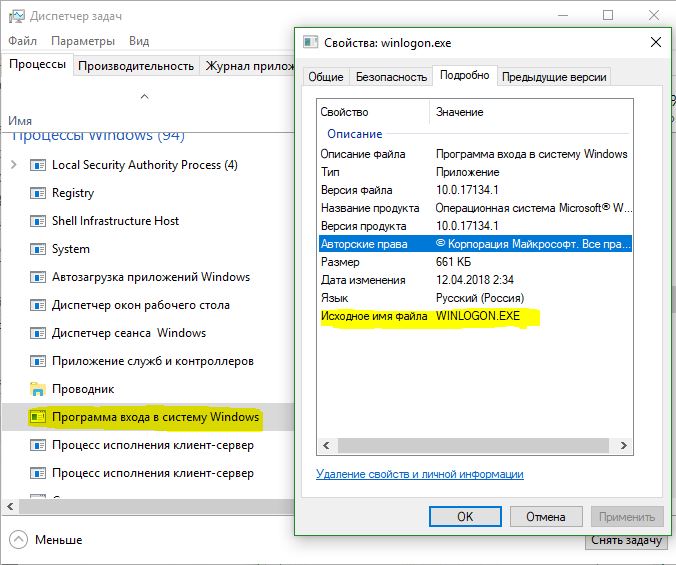
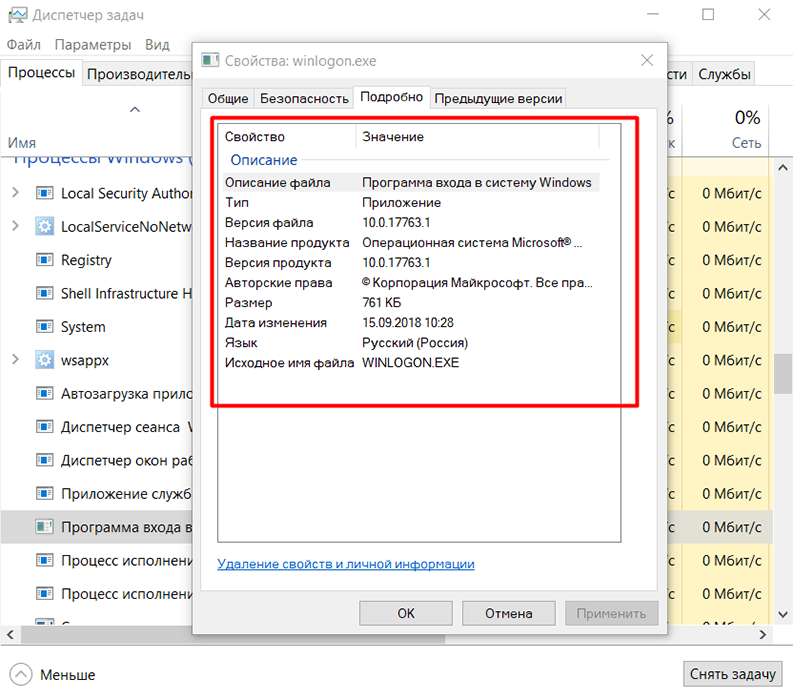
- Right-click on any of the “suspects” and select its “Properties”, then go to the “Details” tab. Particular attention should be paid to the specified author, version and update dates. Microsoft must be listed here.
- Right-click again and select “Open File Locations” to verify that the executable file is “Winlogon.exe”.
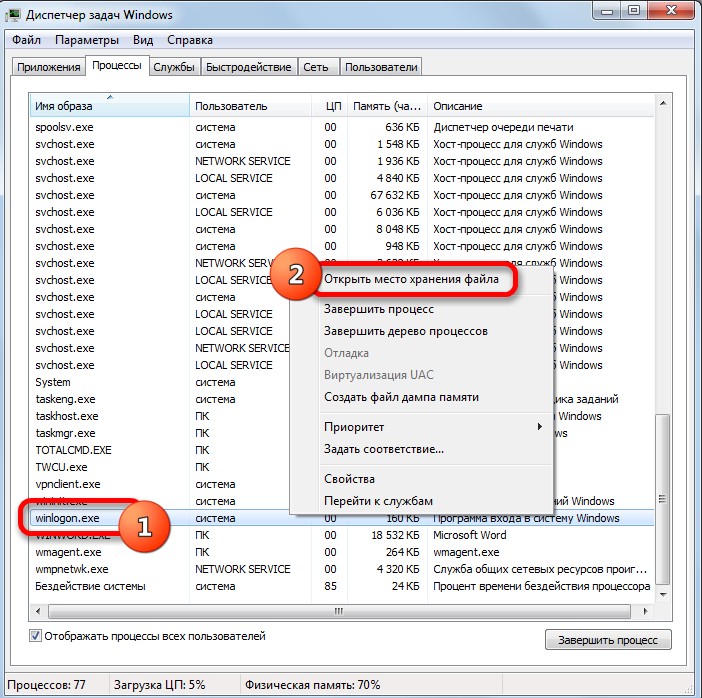
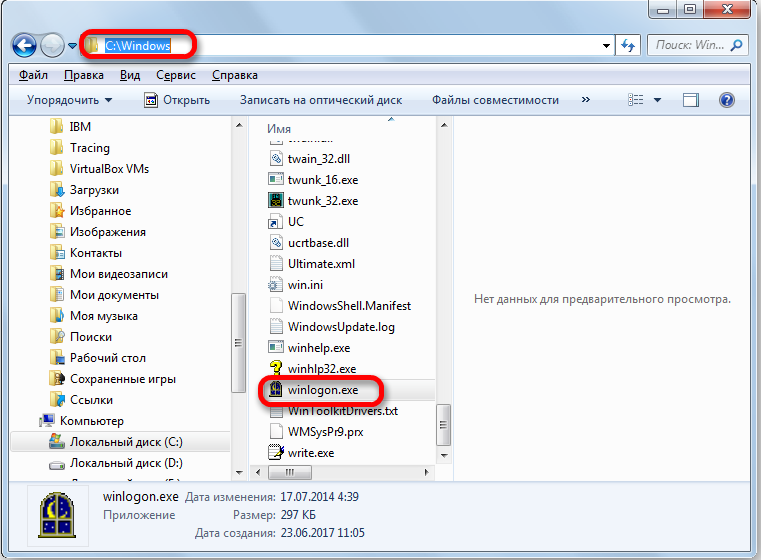
This information is sufficient to verify that there are security gaps in your copy of Windows.
Conclusion
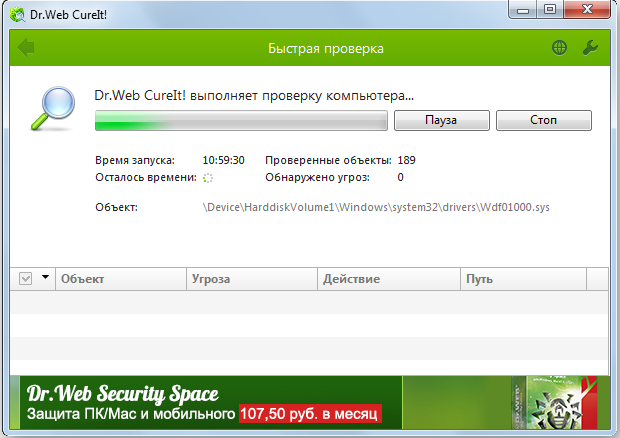
After identifying the intruder, it is required to neutralize it with specialized antivirus software. It is advisable to use third-party utilities that differ from the antivirus presented on your computer, since this defender did not cope with its work and overlooked the “villain”. As a tip, we can mention such utilities as “Dr.Web CureIt!”, “AdwCleaner” and “Malwarebytes”. The last thing you need to make sure of is how well the installed antivirus works, perhaps it needs an update or more powers to function.