Malicious code is supposed to hide behind legitimate apps and thus be able to request authorization to spy. Despite attacks, there is still no patch.
Promon security researchers warn of malware that could address a vulnerability in Android’s multitasking system. All Android versions up to the current edition 10 are to be affected.
If attackers exploit the gap, they could tap microphones from smartphones and record passwords under certain conditions. Promon warns of current attacks of this type. Google should be aware of the vulnerability christened StrandHogg, but according to the security researchers, no security update has yet been announced. The attacks are said to work on just under 94 percent of the most popular apps on Google Play. However, the security researchers do not give any specific names.
Requirements for attack
However, an attack is not easily possible and malicious code must already be on the device. In Google Play, there should have been legitimate apps that bring this malicious code as an additional module, the security researchers say in a message . Which apps are in detail, however, is not there. Google is said to have taken them offline. However, the security researchers assume that such “dropper apps” could reappear in Google Play at any time.
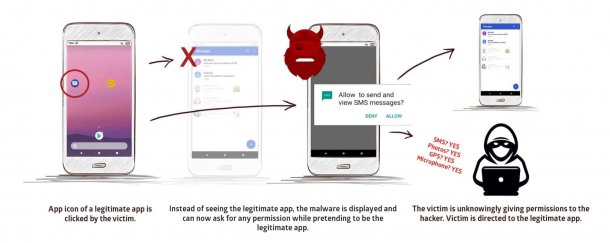
Once the malware is on a device, attackers could attack it remotely. This should be possible without root rights. In doing so, they address a weak point in the multitasking approach of Android. Obviously, no CVE number has yet been assigned for the gap. An attempt to evaluate the risk of attack is also in vain – but the signs all point to “critical”.
What is happening?
If a provider opens a legitimate app, the malicious code should be able to intervene in the multitasking system and thus request authorizations disguised as a legitimate app. For example, attackers could get access to the camera and the victim has no idea what the legitimate app is like. Alternatively, attackers could also replace log-in screens in this way and intercept access data via their own phishing forms. Promon claims to have concrete evidence that attackers are already actively exploiting this.
The exploit is aimed at the multitasking function taskAffinity. Apps can assume any identities in the multitasking system. Coupled with other functions, malicious code can come to the fore in the context of legitimate apps. According to the security researchers, users should not notice anything of this. They explain further details of possible attacks in a detailed report .
