Initially, the dominant function of a mobile phone, voice communication, today, if it has not receded into secondary roles, is certainly not the only one or prevailing. An increasing number of users give preference to the exchange of small messages that do not require a call to the subscriber, which is why it is impossible to imagine a modern smartphone without one or several instant messengers. Among the most popular is the WhatsApp application, which focuses on usability, good functionality, reliability and security. The latter factor is largely implemented through the use of end-to-end encryption, which we will talk about today.

Contents
What is end-to-end encryption and how does it work
In the specialized literature, the term “end-to-end encryption” is not used; this method of data transmission is called end-to-end. In fact, this means that information from the sender to the recipient is transmitted in encrypted form, unlike transport encryption, when encrypted data arrives at an intermediate server, it is decoded there, encrypted again and sent to the recipient. From the point of view of the possibility of breaking the code, both methods can be considered equally safe, but in the latter case, the server is a weak point – its owners can get access to the correspondence if they wish. This is not possible with end-to-end encryption.
Let’s take a look at what end-to-end encryption is in the WhatsApp messenger. So, when the correspondence is initialized, both on the sender’s smartphone and on the recipient’s device, two keys are generated, an open and a private one. An open message is sent to another person in the chat so that he knows how to encode the message so that you can read it. You get exactly the same open code, thanks to which you get the ability to decrypt incoming data.
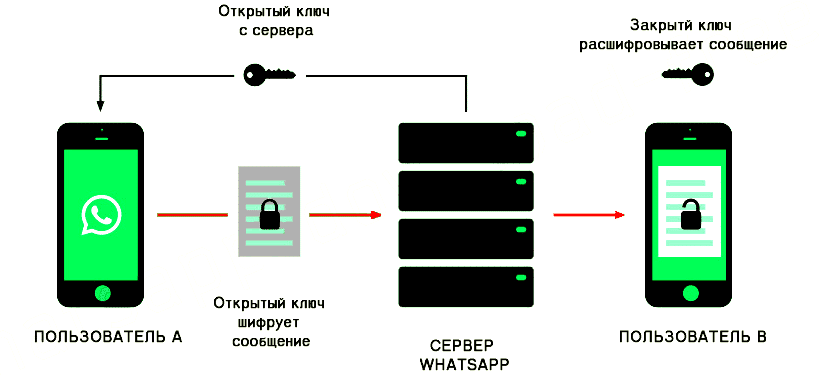
The private key is stored only on the sender’s device and is needed to decode the sent message. The public key can be intercepted, but it only describes how to encrypt the data, the decryption key remains unknown.
This means that the protection of correspondence with end-to-end encryption is one of the most secure ways of exchanging data over open communication channels, although not ideal, we will talk about this a little later.
Why WhatsApp uses end-to-end encryption
Data encryption is a necessary measure to protect sensitive data, but neither search engines nor social networks use the end-to-end method for this. The reason is quite obvious – it is beneficial for them to track user preferences for displaying targeted (targeted) advertising. At the same time, anonymity from the use of this information by a third party is not guaranteed, especially for requests from special services and law enforcement agencies.
Why did WhatsApp decide in 2016 to introduce end-to-end encryption, which means that employees of the company are not able to read user messages?
The formal reason is to improve the security of communication, to protect against cybercriminals seeking to take over personalized data. Although it is rumored that the owners of the messenger (that is, Facebook) decided to take such a step in connection with the conflict with the security forces, which, having access to confidential information, allows you to control the citizens of their countries with or without it.
Note that all types of data are subject to encryption, not just text. To ensure the protection of WhatsApp with end-to-end encryption, the developments of Open Whisper Systems specialists were used, who created the Signal messenger, which at one time was considered the most secure and secure in the world. Since the private security key is stored on a specific device, when one of the interlocutors changes the phone, which often happens, you will have to regenerate it, and this happens automatically on the new phone, and all contacts receive appropriate warnings.
Many people criticize how changing the encryption works on WhatsApp – the warning will be sent only to those users who have this option enabled. It turns out that many will not even know that the contact “name” has changed the phone number and code. And cybercriminals can take advantage of this, because in order to make sure that you received the message from the user who changed the mobile device, you need to check for the coincidence of codes. And you can not even guess about changing the code.
How to check end-to-end encryption
Although Facebook calls such a problem far-fetched, company representatives strongly recommend not to deactivate the option to receive messages from the system, and if you receive such a message, perform a key match check.
It can be done in different ways. For example, rewrite the 60-digit code in the information section and send it to the interlocutor in any other way. Of course, in compliance with security measures. Your counterpart must on his device compare the code you sent with the code on the message. If they match, then everything is in order.
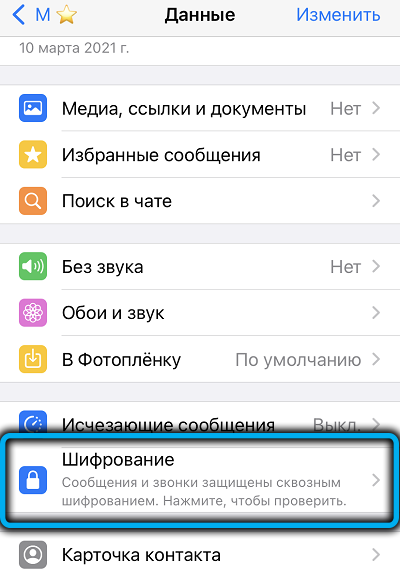
Instead of a digital code, you can send a QR code by clicking the “Share” icon on the display page of this digital code, which resembles a barcode, but consists of randomly spaced squares instead of stripes. If the QR code match check is successful, a green check mark will appear on the page, and this will mean that the messaging is protected.
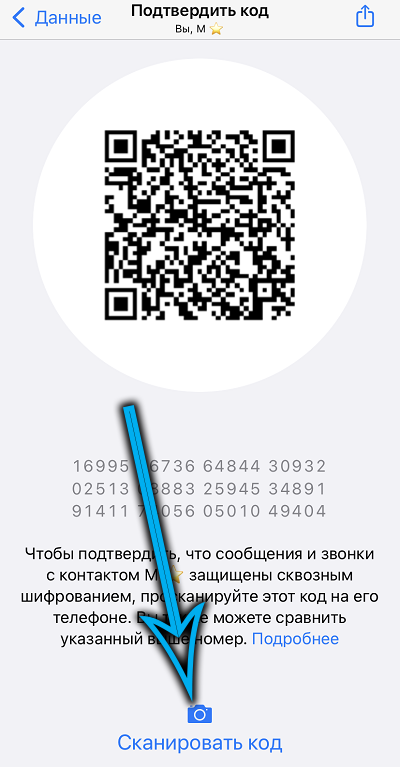
The main problem is precisely how to send a digital or QR code to the interlocutor so that it is not intercepted. The easiest way to do this is in a personal meeting with your contact. In this case, it is enough just to compare the sequence of 60 digits or scan the QR code with your phone. If there is no match, it means that the cipher of some other contact was scanned by mistake. This situation can also arise if the versions of the messenger do not match.
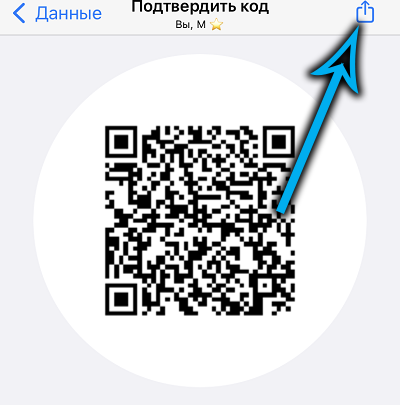
Note that both codes are not a cipher, neither open nor closed – they are only part of the security system designed to authenticate end-to-end encryption, which does not need to be enabled in WhatsApp.
End-to-end encryption limitations in WhatsApp
And yet, there are no absolutely reliable protection systems. Yes, the message itself can be intercepted, but its decoding is associated with such material and time expenditures that it loses its practical meaning. At the same time, the very fact that comrade A forwarded a message to comrade B is not a secret and is recorded on the server. Along with the date and time. This means that if your interlocutor is interested in cybercriminals and law enforcement agencies, then you can also get into their field of vision.
The second limitation is related to the fact that it is enough for someone to take possession of your mobile device, then he will automatically gain access to your correspondence and be able to duplicate it. Therefore, it is so important to lock the phone in inactive mode and use personalized authentication methods such as a fingerprint – in this case, even a stolen phone will not allow an attacker to gain access to sensitive data.
And the third point. Let’s say you take a responsible approach to the security of your wearable device, but no one can give you a guarantee that your contacts are of the same opinion. This means that if your friend’s phone falls into the wrong hands, he can use it for unseemly purposes.
In 2021, the privacy policy of the messenger was completely changed in such a negative way that it led to a massive refusal of users from WhatsApp. The fact is that a clause has appeared in the amended document, according to which some data from WhatsApp will be transferred to Facebook, since it is the parent company.
And although this data does not in any way relate to the content of the correspondence, the very fact of collecting information about the actions of customers did not meet with understanding from the users. At least in the Signal and Telegram messengers, if such metadata is collected, then on a much smaller scale. The reason for the discontent is understandable – Facebook servers are a tidbit for hackers, and if the databases are compromised, as has happened, the confidential data of millions of users could be compromised.
How to remove end-to-end encryption in WhatsApp
We already noted that you don’t need to enable end-to-end encryption in Whatsapp – it’s built into the app. From this it follows that you cannot cancel the data encoding, and is it necessary?

Although there will always be users who consider the inability to remove the encryption as discrimination. There are those who, as an argument against using such reliable security tools, cite the fact that the time for encrypting / decrypting messages is increasing, especially if these are large files such as video that do not need to be protected.
Such users can be advised a quite working way of how to disable end-to-end encryption in WhatsApp: switch to the old version of the messenger – the one where end-to-end encryption has not yet been implemented. Of course, in this case, the functionality of the application will suffer greatly.
It is also worth noting that you will not find such versions on the official Whatsapp website, that is, you will have to look for them on third-party resources, which increases the risk of running into fake software. In any case, you must have activated the “Install from unknown sources” function, available in the developer menu. But this is for Android devices. The iPhone will have to be jailbroken and void of warranty.