Microsoft’s concern for the security of its operating system is understandable: the largest software company decided that they should not trust third-party antivirus software companies to protect their PCs. Alas, Windows Defender, taking on these responsibilities, is not doing very well with threats so far. Yes, with each update it gets better, but at the same time such a trait of his as suspicion only intensifies. And many users do not like this at all.
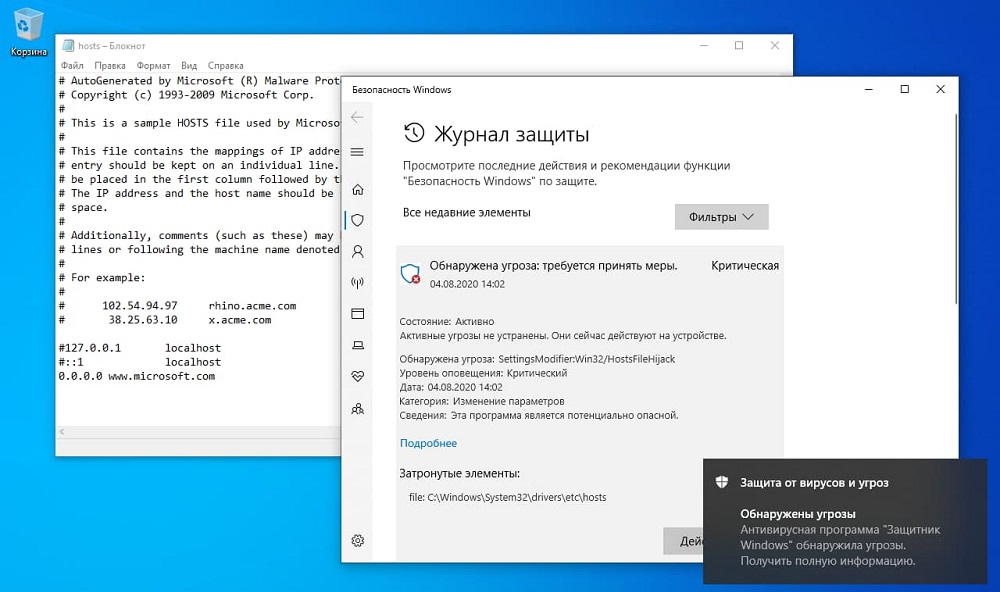
Today we will talk about the SettingsModifier: Win32 / HostsFileHijack error issued by Microsoft Defender, which is directly related to the above.
What is this threat
In computer terminology, the word Hijack is associated with virus software that seeks to seize control of the user’s computer for the most unseemly purposes. For example, to display advertisements or track the actions of the PC owner, or even to steal confidential information, including financial information.
Therefore, if the user sees the inscription SettingsModifier: Win32 / HostsFileHijack on his monitor, he reasonably suspects that he has caught a virus. And he starts looking for information on how to get rid of this malicious code. And very quickly he becomes convinced that, most likely, he himself is the culprit for the appearance of such an error.
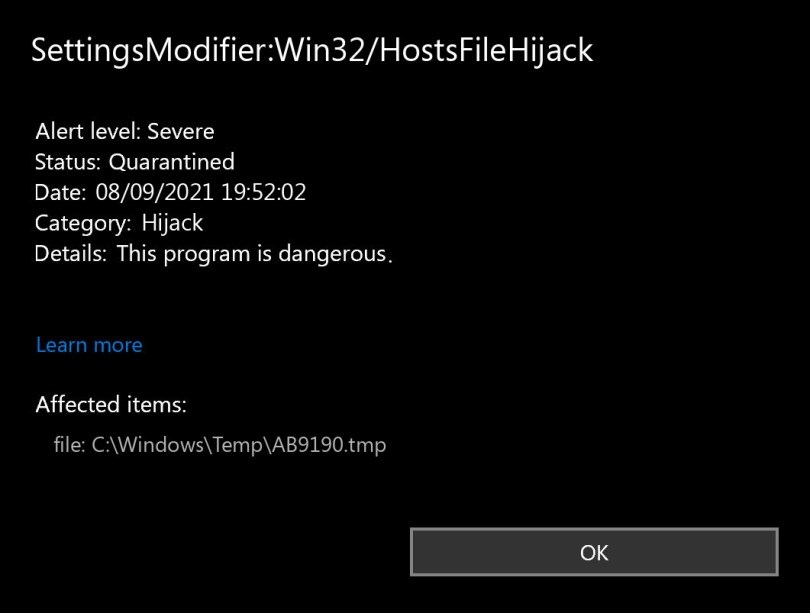
It turns out that Windows 10 Defender reacts in a peculiar way to disabling Microsoft telemetry, performed by blocking access to an entire pool of sites on its own and some other domains. Such messages have become more frequent since the end of July 2020, when the corresponding changes were introduced through the next update of the operating system.
However, Microsoft Defender had tracked changes in the contents of the hosts file before, and quite reasonably classified such actions as a threat. This method of infecting the hosts file is monitored by many antiviruses, for example, Kaspersky Anti-Virus (Trojan.Win32.Qhost) or McAfee, which calls this threat Qhosts.apd.
But if the addition of new lines to the hosts file was previously the subject of analysis for the presence of real threats, now the Defender “swears” at user actions aimed at blocking access from the operating system to the servers responsible for providing the telemetry function.
What is this file and what are its features?
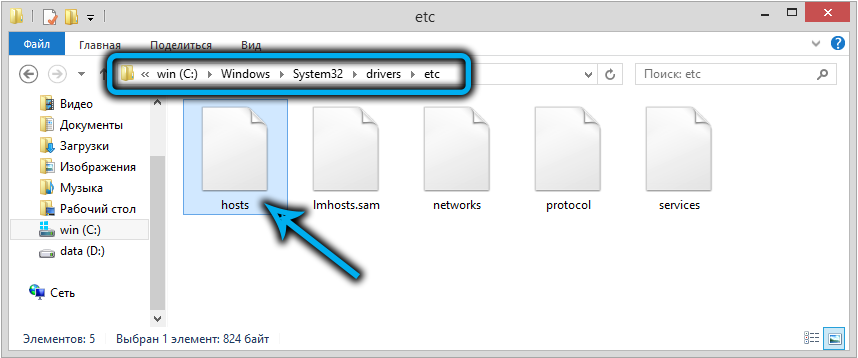
It is present in most operating systems, including Microsoft, starting with the XP version. Its location is unchanged, it is the C: Windows System32 drivers etc directory. The file itself belongs to the system, that is, to edit it, you need to have administrator rights. This is a plain text file in which the site addresses are entered in symbolic form and a digital IP address is assigned to them. The meaning of such actions becomes clear if you know that hosts are processed in the first place, and only then the operating system redirects the request using the domain name system, that is, DNS. The most obvious way to use the file is to block access to certain sites, which can be achieved by assigning them to a local IP address like 127.0.0.1 or the nonexistent 0.0.0.0.
But this feature is also used by viruses, introducing lines into hosts that allow the user to redirect to a different site than the one he typed in the address bar, that is, to make a clever redirect.
So keeping track of the contents of this file is a really necessary job. But in our case, Windows regarded an attempt to block access to servers owned by Microsoft and tracking telemetry at the level of editing the hosts file as a threat.
The problem was not immediately discovered, but it soon became clear that the SettingsModifier: Win32 / HostsFileHijack warning would appear if the user denied access to any of the software giant’s large list of domains and subdomains:
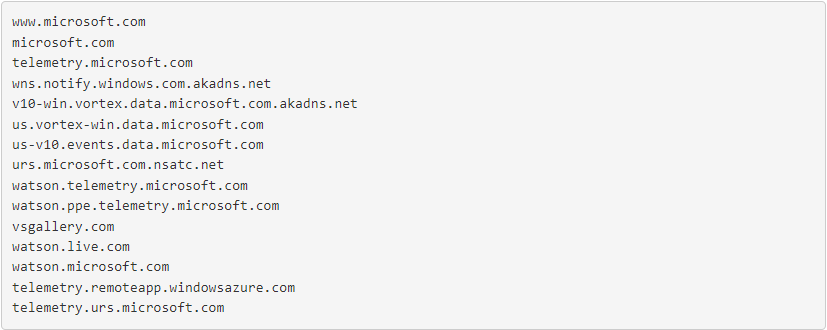
And although the message claims the level of threat as critical, this, of course, does not correspond to reality, since such actions are taken by users on their own initiative with the sole purpose of not allowing them to track their activities, even if it is done with the most plausible intentions. Which the majority, of course, doubt.
What to do if a message appears
When a threat message appears, you are simultaneously prompted to choose one of three possible scenarios (this is the standard Windows Defender response to such situations):
- Delete.
- Move to quarantine.
- Allow on device.
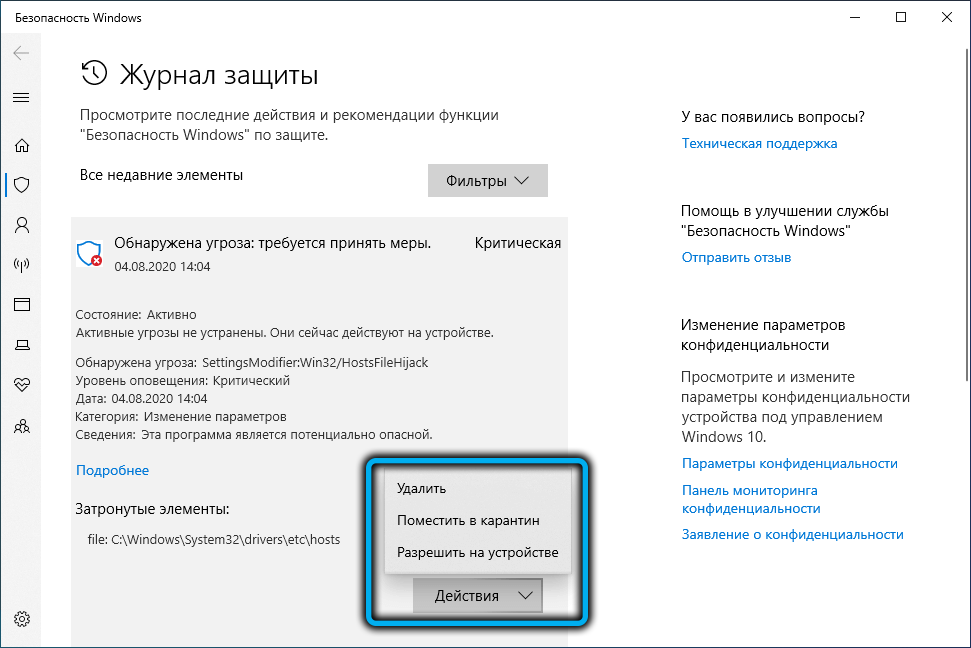
If you select the first option, then if a virus is detected, the Defender will try to remove it. In our case, it will simply restore the hosts file to the state it had immediately after installing Windows, that is, all the entries you added will be erased. Including those that blocked telemetry.
When you select “Move to Quarantine”, the infected file is moved to a special place where it cannot be active. But since we have a file that the operating system needs, it will again be restored to its default state.
By selecting “Allow Usage”, you ask the Defender to leave things as they are. That is, do nothing with the hosts file, which you edited in accordance with your beliefs.
If you chose the third option, be prepared for this message to appear again. How do I remove the error? Only by canceling the blocking of Microsoft sites. Although there is an alternative solution: to refuse to use the Defender altogether, we will not recommend this option. Even if you have good antivirus software installed that has served you faithfully for many years.