Just started working as a network administrator? Don’t want to be confused? Our article will be useful to you. Have you heard how a time-tested administrator talks about network problems and mentions some levels? Have you ever been asked at work what levels are protected and working if you are using an old firewall? To understand the basics of information security, you need to understand the principle of the hierarchy of the OSI model. Let’s try to see the capabilities of this model.
A self-respecting sysadmin should be well versed in networking terms
Contents
OSI network model
Translated from English – the basic reference model for the interaction of open systems. More precisely, the network model of the OSI / ISO network protocol stack. Introduced in 1984 as a conceptual framework that divided the process of sending data on the World Wide Web into seven simple steps. It is not the most popular, since the development of the OSI specification was delayed. The TCP / IP protocol stack is more cost effective and is considered the primary model used. However, you have a huge chance of encountering the OSI model as a system administrator or in the IT field.
Many specifications and technologies have been created for network devices. It’s easy to get confused with such a variety. It is the model of interaction of open systems that helps network devices to understand each other using various methods of communication. Note that OSI is most useful for software and hardware manufacturers who design interoperable products.
Ask, what is the benefit to you? Knowledge of the multi-level model will give you the opportunity to freely communicate with employees of IT companies, discussing network problems will no longer be depressing boredom. And when you learn to understand at what stage the failure occurred, you can easily find the causes and significantly reduce the range of your work.
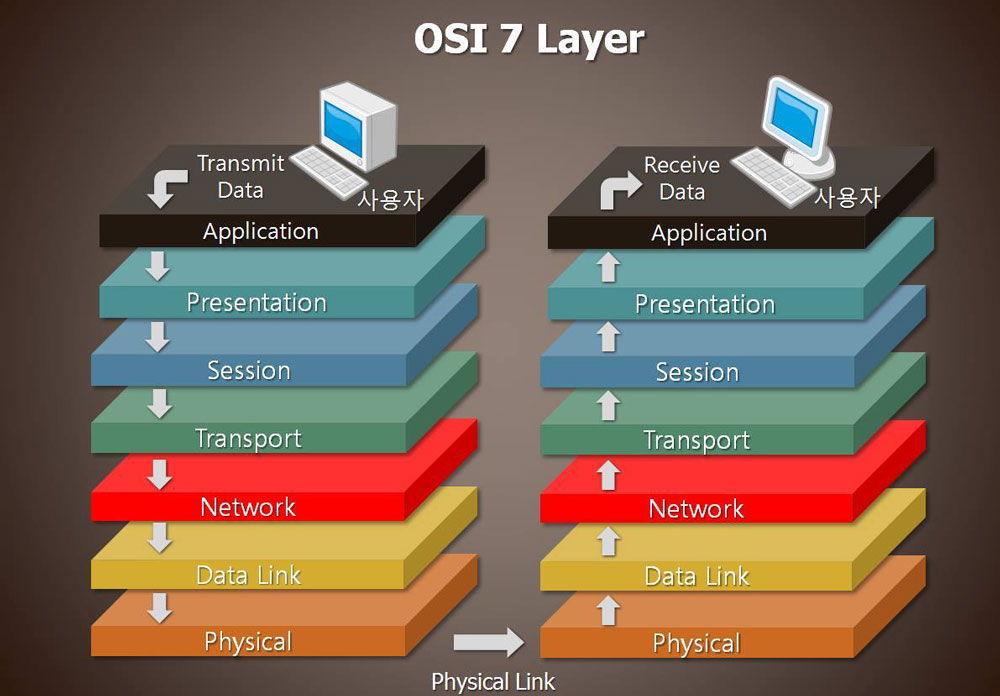
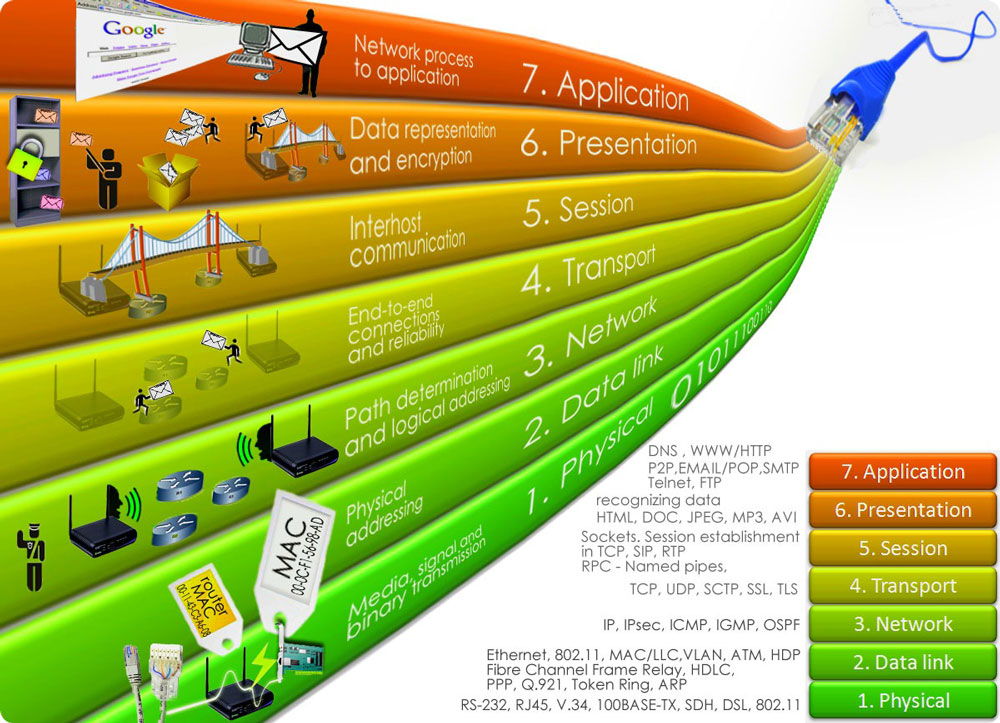
OSI layers
The model contains seven simplified steps:
- Physical.
- Channel.
- Network.
- Transport.
- Session.
- Executive.
- Applied.
Why does decomposition into steps make life easier? Each of the levels corresponds to a certain stage of sending a network message. All steps are sequential, which means that the functions are performed independently, there is no need for information about the work at the previous level. The only necessary component is how the data from the previous step is received, and how the information is sent to the next step.
Let’s move on to direct acquaintance with the levels.
Physical layer
The main task of the first stage is the transfer of bits through physical communication channels. Physical communication channels are devices designed to transmit and receive information signals. For example, optical fiber, coaxial cable, or twisted pair. The transfer can also take place wirelessly. The first stage is characterized by the data transmission medium: anti-interference, bandwidth, characteristic impedance. The qualities of the electrical final signals (type of coding, voltage levels and signal transmission rate) are also set and connected to standard types of connectors, contact connections are assigned.

The functions of the physical stage are carried out absolutely on every device connected to the network. For example, a network adapter implements these functions from the computer side. You may have already come across the first step protocols: RS-232, DSL and 10Base-T, which determine the physical characteristics of the communication channel.
Link layer
At the second stage, the abstract address of the device is associated with the physical device, and the availability of the transmission medium is checked. Bits are formed into sets – frames. The main task of the link layer is to identify and correct errors. For correct transmission, before and after the frame, specialized bit sequences are inserted and the calculated checksum is added. When the frame reaches the destination, the checksum of the already arrived data is calculated again, if it matches the checksum in the frame, the frame is recognized as correct. Otherwise, an error appears, which can be corrected by re-transmission of information.

The channel stage makes it possible to transfer information, thanks to the special structure of the links. In particular, buses, bridges, switches work through the link-level protocols. The second step specifications include Ethernet, Token Ring, and PPP. The functions of the channel stage in the computer are performed by network adapters and their drivers.
Network layer
In standard situations, the functions of the channel stage are not enough for high-quality information transfer. The specifications of the second step can only transfer data between nodes with the same topology, for example, a tree. There is a need for a third stage. It is necessary to form a united transport system with a branched structure for several networks with an arbitrary structure and differing in the method of data transfer.

Если объяснить по-другому, то третий шаг обрабатывает интернет-протокол и исполняет функцию маршрутизатора: поиск наилучшего пути для информации. Маршрутизатор — устройство, собирающее данные о структуре межсетевых соединений и передающее пакеты в сеть назначения (транзитные передачи — хопы). Если вы сталкиваетесь с ошибкой в IP-адресе, то это проблема, возникшая на сетевом уровне. Протоколы третьего этапа разбиваются на сетевые, маршрутизации или разрешения адресов: ICMP, IPSec, ARP и BGP.
Транспортный уровень
Чтобы данные дошли до приложений и верхних уровней стека, необходим четвёртый этап. Он предоставляет нужную степень надёжности передачи информации. Значатся пять классов услуг транспортного этапа. Их отличие заключается в срочности, осуществимости восстановления прерванной связи, способности обнаружить и исправить ошибки передачи. К примеру, потеря или дублирование пакетов.

Как выбрать класс услуг транспортного этапа? Когда качество каналов транспортировки связи высокое, адекватным выбором окажется облегчённый сервис. Если каналы связи в самом начале работают небезопасно, целесообразно прибегнуть к развитому сервису, который обеспечит максимальные возможности для поиска и решения проблем (контроль поставки данных, тайм-ауты доставки). Спецификации четвёртого этапа: TCP и UDP стека TCP/IP, SPX стека Novell.
The union of the first four levels is called the transport subsystem. It fully provides the selected level of quality.
Session level
The fifth stage helps in regulating dialogues. It is impossible for the interlocutors to interrupt each other or speak synchronously. The session layer remembers the active side at a specific moment and synchronizes information, coordinating and maintaining connections between devices. Its functions allow you to return to a checkpoint during a long transfer and not start over. Also, at the fifth stage, you can terminate the connection when the exchange of information is completed. Session-level specifications: NetBIOS.

Representative level
The sixth stage is involved in transforming data into a universal recognizable format without changing the content. Since different devices utilize different formats, the information processed at the representative level makes it possible for the systems to understand each other, overcoming syntactic and code differences. In addition, at the sixth stage, it becomes possible to encrypt and decrypt data, which ensures secrecy. Examples of protocols: ASCII and MIDI, SSL.

Application level
The seventh stage on our list and the first if the program sends data over the network. Consists of a set of specifications through which the user gains access to files, Web pages. For example, when sending messages by mail, it is at the application level that a convenient protocol is selected. The composition of the specifications for the seventh stage is very diverse. For example, SMTP and HTTP, FTP, TFTP, or SMB.
You may hear somewhere about the eighth level of the ISO model. Officially, it does not exist, but a comic eighth stage has appeared among IT workers. All due to the fact that problems can arise through the fault of the user, and as you know, a person is at the pinnacle of evolution, so the eighth level appeared.

Having looked at the OSI model, you were able to understand the complex structure of the network and now you understand the essence of your work. It gets pretty easy when the process is broken down!