In order to ensure the safe operation of Internet resources, each responsible user installs a Firewall or an antivirus product on his PC, choosing an acceptable protection option from those offered by the developers. In this article, we will focus on a product that successfully stands out for the reliability of protection against the background of similar ones, namely about Comodo Firewall, its advantages and differences, features of installation, configuration and operation.
Contents
Comodo Firewall Features
The fundamental task of Firewall is to reliably protect your computer from external threats, of which there are many on the Internet resources. Naturally, fundamental and effective protection are the main qualities that justify the popularity of a particular product. Why Comodo Firewall should be chosen from an assortment of similar tools for purpose and protection criteria lies in the key features of the product:
- The product serves as a fundamental defense tool against Internet threats of any category, including new modifications of viruses.
- The product at the highest level implements the ability to check and scan “dubious” codes through a special cloud service.
- Comodo Firewall has so-called “white” codes, the number of which is more than fifteen million, which allows the software to recognize an unauthorized element trying to enter the system and block it at the initial stage of implementation into the software.
- A powerful and reliable packet detection and filtering system guarantees security by blocking connections from dubious addresses.
- Comodo Firewall is optimized for all versions of operating systems, including Windows 10.
In addition to these features, the advantage of the product is its active and regular updates by developers, aimed at perceiving and identifying new “dangerous” elements that appear on the network every day.
Differences from other Firewalls
Despite the many positive reviews and advantageous positions, many are wondering why it is worth giving preference to the Comodo Firewall tool over another software product. It is worth noting that Comodo Firewall is a very powerful and reliable application among free counterparts, not inferior in level of protection to paid versions of Firewall from other developers. Ease of use is complemented by the presence of a Russian-language interface, which allows you to understand the settings of the program yourself, to set priority protection settings. An important criterion for many users is the size of the program: Firewall, against the background of excellent security parameters, has little weight, and the ability to operate it in an economical mode of resource consumption allows you to install it even on a PC with low technical performance.And as a verdict in favor of choosing Comodo: unlike others, the program is a modified and independent tool, which is far from characteristic of Firewall from other developers.
Downloading and Installing Comodo Firewall
The issue of downloading the product almost never causes difficulties for the consumer: Firewall is free, and it is better to download it from the official website of the developer . After waiting for the end of the download of the product, you can proceed with the installation, which is not difficult, but there are some nuances. After double-clicking on the downloaded file, and after a few seconds of waiting, which will take to unpack the application files, the “Installation Wizard” window will open, where you will initially need to select the interface language.
At the next stage, a window will open where the checkboxes are marked on the anonymity of sending changes that increase the efficiency of the application, as well as on the possibility of cloud analysis of application data. Here the user, at his discretion, can check or uncheck the boxes: these parameters will not be reflected in any way on the efficiency of the application. It is important to enter the “Configure installation” menu, in which the user will be able to activate the components necessary for operation:
- In the “Installation Options” tab, you must leave a tick only opposite the “Install Comodo Firewall” item.
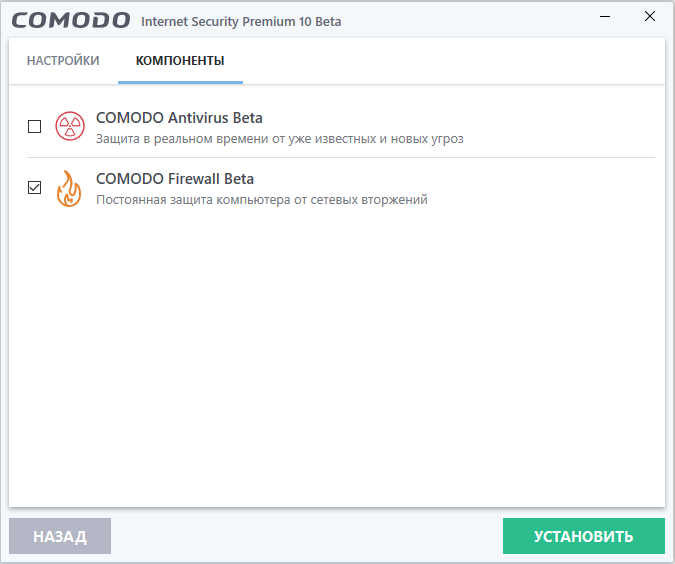
- In the menu “Configuration options” activate the item “Do not show alerts requiring the user to make security decisions”.
- In the “File location” item, select the preferred localization of the installation components of the program.
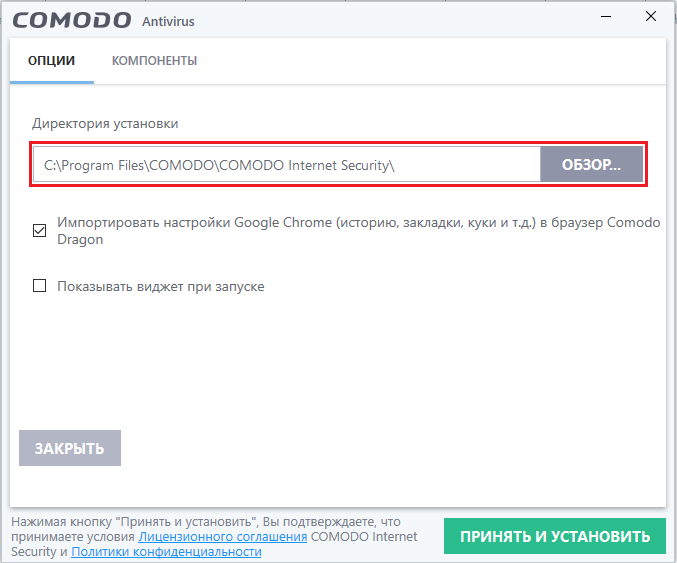
After the performed manipulations, you need to return using the “Back” button to the start installation window, where to continue the installation by clicking “Next”. In the next window, the program will offer to install Yandex components, which is optional, and proceed to the final stage of the installation by pressing the “Install” command.

After the installation is complete, the Firewall will automatically start and ask you to restart the PC, which must be done to start the program.
Initial settings
The program requires mandatory initial configuration, which must be performed after restarting the PC. After rebooting, you will see the program window on the screen with the notice “Under protection”, indicating the operation of the application, and the manufacturer’s website will open.
Next, you will need to select the level of protection among those offered by the program. The position “I am in a public place” has the highest confidentiality parameters, which is recommended to be chosen to ensure PC security. When the program is running, the user will receive messages in which the program signals an attempt to connect to a specific browser, site or other object, where you can confirm the connection or reject it to block, depending on the situation:
- If the program tries to connect to an element or site known to the user, then it is worth “Allow operation”.
- If the Firewall asks for permission to connect to an “incomprehensible” component, which is incomprehensible even after searching the network for information, then it is better to block the process.
Next, you need to configure the correct functioning of Comodo Firewall:
- Open the main Comodo menu by right-clicking on the active program window and select “Open” from the drop-down list.
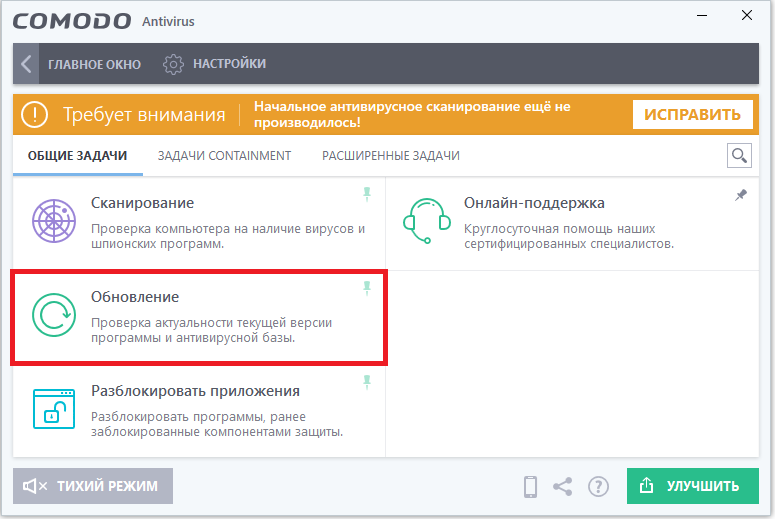
- In the main window, through the “Tasks” menu, it is necessary to update the program to the latest version.
- In the same window, you can run a computer scan to identify real or potential threats to your PC.
It does not hurt to configure the component “Launch in a virtual environment”, which will allow the user to wander around “dubious” sites, without fear of infection. To do this, you will need to click on this function, select and launch an application or site that requires login in virtual, isolated mode, create a shortcut to enter this environment on the desktop, which will eliminate the need for regular input of parameters, with the expected frequent use of a particular “questionable” applications. The button located in the upper left corner of the main window allows you to switch between tasks, monitor the protection status and the number of connections, manage application options and adjust secondary settings that may be relevant at a particular stage of PC operation.
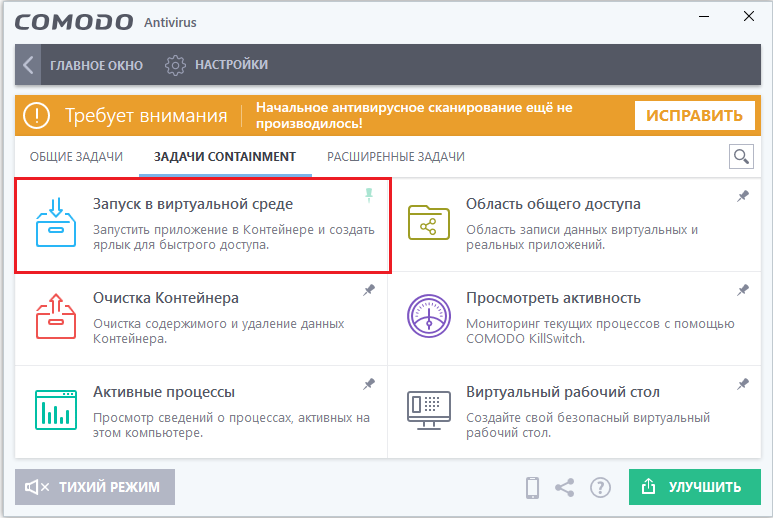
Additional settings
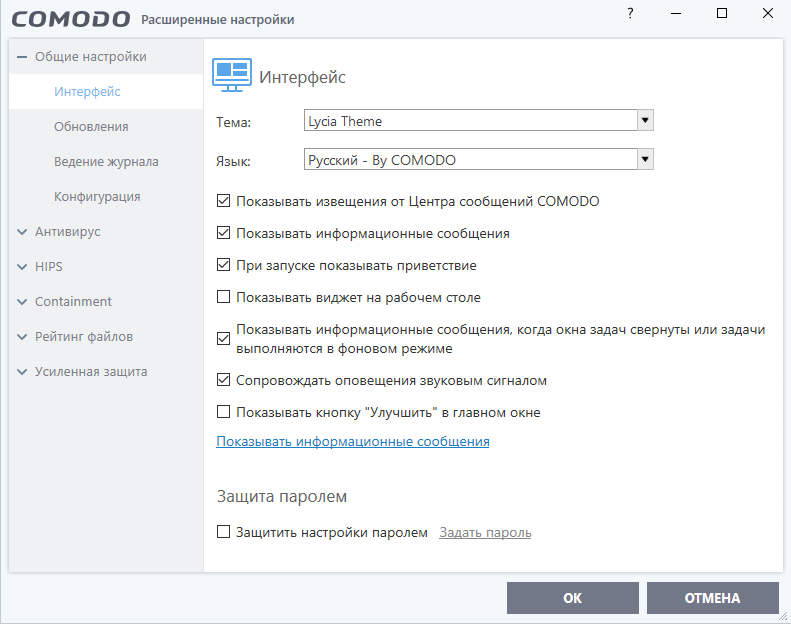
After the basic functionality of Comodo Firewall is configured, with a mandatory update, a scan, and a security level setting, the program will by default protect the operating system from threats. These settings are sufficient for the correct functioning of the Firewall, but during operation, the user’s requirements may increase, which creates the need to parse additional settings. For example, some discomfort when using the application is caused by the sound of the Firewall: the sound can be turned off in the General settings menu in the Interface item. In the same place, you can remove from the tasks the launch of the greeting program every time the computer is turned on and some similar items that do not affect the functioning of the software.
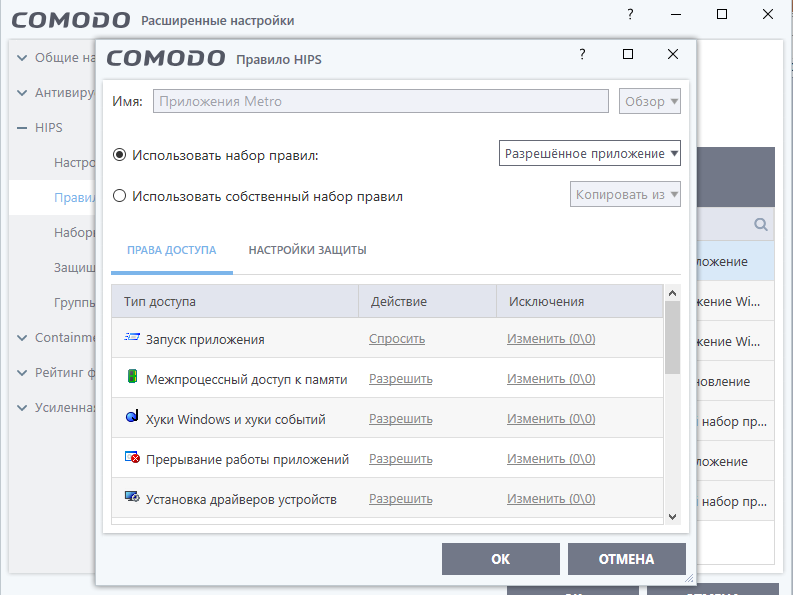
It is recommended that you configure the HIPS tool that is responsible for intrusion prevention. If the program is installed on a low-power PC, in the instrument settings, you must select the item “Adapt the mode of operation with low system resources”, or set the economical mode of resource consumption. The “Content Filter” function allows you to block or include in the allowed specific sites. This point is relevant when using a computer by several users: it allows you to block children’s access to certain content or prohibit the download of obviously “dangerous” sites. In the “Firewall” tab, you can configure the frequency of messages, activate the IPV6 traffic filter and block against falsified ARP, as well as the option to create rules for applications. You can set, adjust or delete prescriptions,relevant for a particular application.
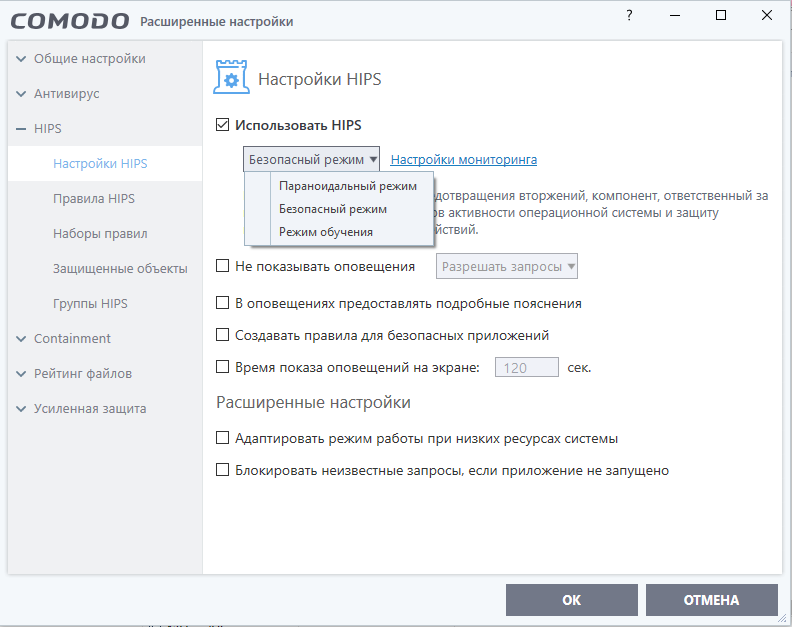
As for the more precise and detailed settings of the program, any user can study them by selecting “Training Mode” in the application settings – this will allow you to thoroughly understand the nuances and features of the security program. If there is no desire to learn, then choose “Safe Mode”, which implies operating the program in a standard mode, with a guarantee of a decent level of protection provided by the developers.
Removing a program
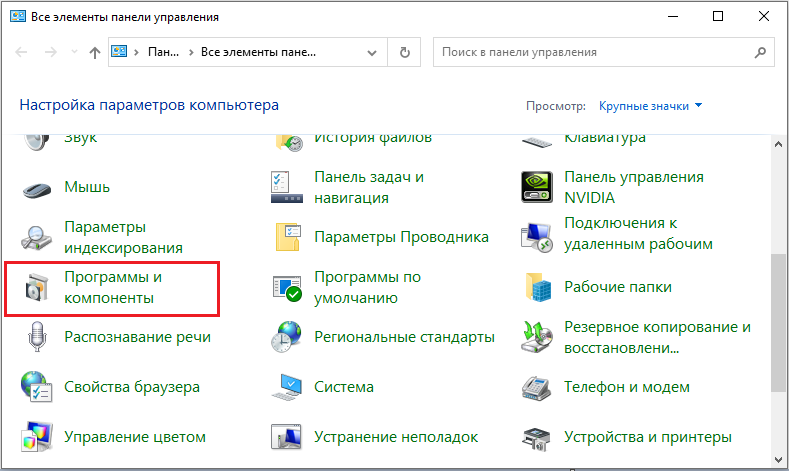
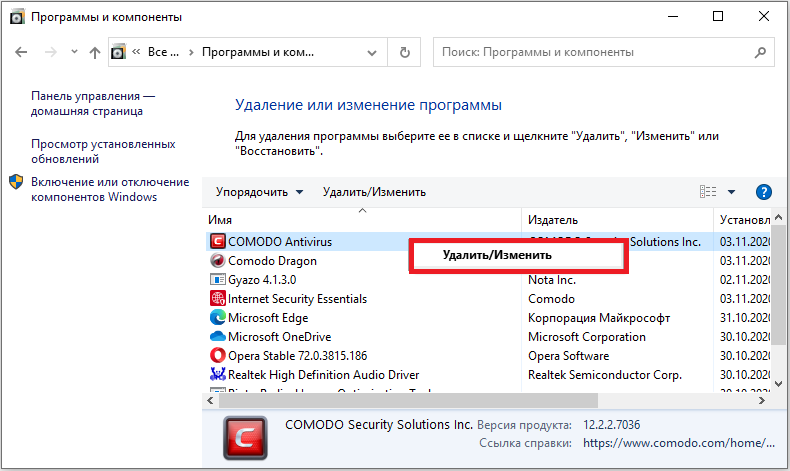
You may need to completely remove Comodo Firewall. It can be removed in the same way as other programs and applications, by entering through the “Start” menu in the “Control Panel”, where you will need to go to “Programs and Features”: find the software in the list, select it and click “Remove”. Next, you will need to confirm the deletion by pressing “Yes” or Yes, agree with the uninstall request and restart the computer for the changes to take effect. This option does not always give a 100% result, since after deletion, traces of the application in the system may remain.
As an alternative, more efficient option, you can use the resources of special programs, for example, CCleanner, Uninstaller, or similar ones for their intended purpose. After performing the manipulations, it is necessary to reboot the computer, with the subsequent elimination of the remaining “tails” of the Firewall. An effective program should be involved in removing traces, for example, the already mentioned CCleanner utility. To uninstall traces, you need to launch CCleanner, go to “Cleanup”, find the application in the registry, start the “Analysis” process and, at the end of the operation, press the “Clean” command. After that, all the contents of the program will be completely deleted from the PC.
Summarizing
Comodo Firewall is an effective program that is constantly updated by developers to meet the innovative needs of protecting computer devices for both home and corporate work. The only obstacle to the use of software is a very old PC configuration, with an unsatisfactory technical base, but such cases are extremely rare in modern times.
Download, install, use and test the strength of active, reliable application protection: the free Comodo Firewall is one of the best in its class.